Comment sécuriser les données d’une application mobile ?
08/07/2021
5min
Tables des matières
- Bonne pratique n°1pour sécuriser ses données : analyser les risques en amont
- Bonne pratique n°2 : mettre en place un système d’authentification fiable pour ses données
- Bonne pratique n°3 : réduire les autorisations de l’application au strict minimum
- Bonne pratique n°4 : sécuriser les données stockées
- Bonne pratique n°5 : tester la sécurité régulièrement et maintenir un suivi continu sur son application
Comment sécuriser les données d’une application mobile ? À l’ère de l’hyper-connectivité, la question de la protection des données est une constante de la cybersécurité. Les exemples de piratages massifs ne manquent pas, comme en mai 2020 où une application d’identification d’appels sur smartphone a signalé une violation de sécurité. Les données personnelles de plus de 47,5 millions d’utilisateurs ont alors été exposées au vol. La sécurité des données d’une application doit aujourd’hui être maintenue tout au long du cycle de vie de développement (ou ADLC, pour Application Development Life Cycle) et ce, bien après son téléchargement par l’utilisateur final. Rassurez-vous : il existe de nombreuses façons d’améliorer efficacement la sécurité des données sur une application mobile, sans pour autant compromettre l’expérience utilisateur.
Bonne pratique n°1pour sécuriser ses données : analyser les risques en amont
Bonne pratique n°2 : mettre en place un système d’authentification fiable pour ses données
Il existe pléthore de systèmes d’authentification très fiables. Toutefois, il est recommandé d’utiliser des procédés qui combinent forte fiabilité et expérience utilisateur fluide. À cet effet, 4 systèmes d’authentification se détachent des autres :
- la biométrie : elle repose sur les caractéristiques biologiques uniques de l’utilisateur. Ce système extrêmement fiable génère peu de friction dans le parcours utilisateur ;
- le QR code : très apprécié des secteurs où les données peuvent être très sensibles (banque, assurance, messagerie, etc.) ;
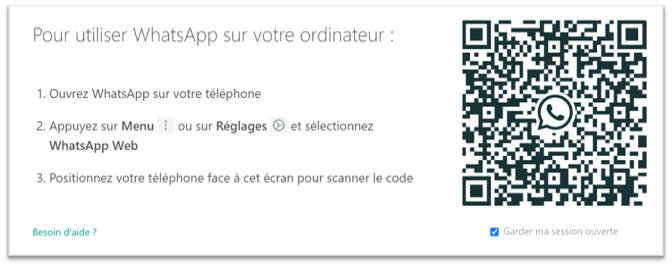
L’authentification par QR code sur WhatsApp Web
- l’OTP (One-Time Password) par SMS : aujourd’hui très répandu, ce système consiste à envoyer un SMS sur l’appareil mobile de l’utilisateur. Le message transmis contient l’information permettant de finaliser le procédé d’authentification ;
- l’authentification comportementale : elle consiste à vérifier l’identité d’un utilisateur sur la base d’un schéma unique à composer. Il s’agit du système d’identification le plus (sans friction) des quatre.
Bonne pratique n°3 : réduire les autorisations de l’application au strict minimum
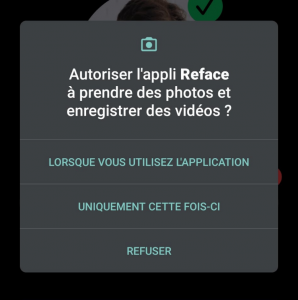
Exemple de demande d’autorisation sur le système d’exploitation Android (Reface)
Certaines fonctionnalités nécessitent l’accord de l’utilisateur pour fonctionner de façon optimale. Toutefois, chacune de ces autorisations représente autant d’opportunités de vol de données sensibles par des pirates informatiques.
À l’image principe du moindre privilège, une application ne doit pas demander plus de prérogatives que le minimum nécessaire à son fonctionnement.
Bonne pratique n°4 : sécuriser les données stockées
Exemple de modèle de chiffrement de données (source : Wikipedia)
Plus la quantité de données stockées est élevée, plus votre application s’expose à des fuites de données. Pour éviter que des personnes malintentionnées ne se les procurent, il faut les rendre inexploitables : c’est le principe du chiffrement des données. Dans la pratique, il existe 2 manières fiables de tirer profit du chiffrement dans un projet de développement d’application :
- le chiffrement en amont (ou Shift-left cryptography) : intégrer le chiffrement dans le processus-même de développement d’une application ;
- le double chiffrement : les systèmes d’exploitation Androïd et iOS fournissent d’office une couche de cryptage aux développeurs d’applications. Toutefois, il est recommandé de doubler ce procédé de sécurité afin de réduire drastiquement le risque d’exposition aux tentatives de vol de données.
Bonne pratique n°5 : tester la sécurité régulièrement et maintenir un suivi continu sur son application
À l’image du test continu en DevOps, la sécurité de votre application doit être une constante à ne jamais négliger, que ce soit avant, pendant ou après la phase de développement. Pour ce faire, il est nécessaire d’investir dans divers tests techniques à effectuer tout au long de cycle de vie de votre application : analyse de vulnérabilité, tests de pénétration, tests d’intrusion, etc.
Sécurité mobile et « Blockchain » : future alliance indispensable ?
Lorsque les applications sont développées à l’aide de la « Blockchain », la confidentialité des données peut être renforcée, ce qui les rend plus sûres. La technique de chiffrement propre à cette technologie est considérée comme l’une des plus sûres à ce jour car toutes les données sont codées et sauvegardées avec un hachage cryptographique. Grâce à son architecture décentralisée, la stabilité des applications tierces est ainsi renforcée. En outre, avec la « Blockchain », un horodatage est attaché à chaque transaction, ce qui rend la manipulation des données et la redéfinition des opérations presque impossible. Seul bémol : les développeurs d’applications mobiles compétents maîtrisant la technologie « Blockchain » demeurent encore rares.
La sécurité des données d’une application mobile est un sujet central. Il doit être considéré en amont du développement jusqu’à la fin du cycle de vie de cette dernière, et ce, de manière continue.
Pour faire face à cet enjeu , il est essentiel de s’entourer d’experts en cybersécurité. Vous cherchez à consolider la sécurité de votre application mobile ? Discutez de votre projet avec nos spécialistes en cybersécurité !
Comment sécuriser les données d’une application mobile ?
08/07/2021
5min
Tables des matières
- Bonne pratique n°1pour sécuriser ses données : analyser les risques en amont
- Bonne pratique n°2 : mettre en place un système d’authentification fiable pour ses données
- Bonne pratique n°3 : réduire les autorisations de l’application au strict minimum
- Bonne pratique n°4 : sécuriser les données stockées
- Bonne pratique n°5 : tester la sécurité régulièrement et maintenir un suivi continu sur son application
Comment sécuriser les données d’une application mobile ? À l’ère de l’hyper-connectivité, la question de la protection des données est une constante de la cybersécurité. Les exemples de piratages massifs ne manquent pas, comme en mai 2020 où une application d’identification d’appels sur smartphone a signalé une violation de sécurité. Les données personnelles de plus de 47,5 millions d’utilisateurs ont alors été exposées au vol. La sécurité des données d’une application doit aujourd’hui être maintenue tout au long du cycle de vie de développement (ou ADLC, pour Application Development Life Cycle) et ce, bien après son téléchargement par l’utilisateur final. Rassurez-vous : il existe de nombreuses façons d’améliorer efficacement la sécurité des données sur une application mobile, sans pour autant compromettre l’expérience utilisateur.
Bonne pratique n°1pour sécuriser ses données : analyser les risques en amont
Bonne pratique n°2 : mettre en place un système d’authentification fiable pour ses données
Il existe pléthore de systèmes d’authentification très fiables. Toutefois, il est recommandé d’utiliser des procédés qui combinent forte fiabilité et expérience utilisateur fluide. À cet effet, 4 systèmes d’authentification se détachent des autres :
- la biométrie : elle repose sur les caractéristiques biologiques uniques de l’utilisateur. Ce système extrêmement fiable génère peu de friction dans le parcours utilisateur ;
- le QR code : très apprécié des secteurs où les données peuvent être très sensibles (banque, assurance, messagerie, etc.) ;

L’authentification par QR code sur WhatsApp Web
- l’OTP (One-Time Password) par SMS : aujourd’hui très répandu, ce système consiste à envoyer un SMS sur l’appareil mobile de l’utilisateur. Le message transmis contient l’information permettant de finaliser le procédé d’authentification ;
- l’authentification comportementale : elle consiste à vérifier l’identité d’un utilisateur sur la base d’un schéma unique à composer. Il s’agit du système d’identification le plus (sans friction) des quatre.
Bonne pratique n°3 : réduire les autorisations de l’application au strict minimum

Exemple de demande d’autorisation sur le système d’exploitation Android (Reface)
Certaines fonctionnalités nécessitent l’accord de l’utilisateur pour fonctionner de façon optimale. Toutefois, chacune de ces autorisations représente autant d’opportunités de vol de données sensibles par des pirates informatiques.
À l’image principe du moindre privilège, une application ne doit pas demander plus de prérogatives que le minimum nécessaire à son fonctionnement.
Bonne pratique n°4 : sécuriser les données stockées

Exemple de modèle de chiffrement de données (source : Wikipedia)
Plus la quantité de données stockées est élevée, plus votre application s’expose à des fuites de données. Pour éviter que des personnes malintentionnées ne se les procurent, il faut les rendre inexploitables : c’est le principe du chiffrement des données. Dans la pratique, il existe 2 manières fiables de tirer profit du chiffrement dans un projet de développement d’application :
- le chiffrement en amont (ou Shift-left cryptography) : intégrer le chiffrement dans le processus-même de développement d’une application ;
- le double chiffrement : les systèmes d’exploitation Androïd et iOS fournissent d’office une couche de cryptage aux développeurs d’applications. Toutefois, il est recommandé de doubler ce procédé de sécurité afin de réduire drastiquement le risque d’exposition aux tentatives de vol de données.
Bonne pratique n°5 : tester la sécurité régulièrement et maintenir un suivi continu sur son application
À l’image du test continu en DevOps, la sécurité de votre application doit être une constante à ne jamais négliger, que ce soit avant, pendant ou après la phase de développement. Pour ce faire, il est nécessaire d’investir dans divers tests techniques à effectuer tout au long de cycle de vie de votre application : analyse de vulnérabilité, tests de pénétration, tests d’intrusion, etc.
Sécurité mobile et « Blockchain » : future alliance indispensable ?
Lorsque les applications sont développées à l’aide de la « Blockchain », la confidentialité des données peut être renforcée, ce qui les rend plus sûres. La technique de chiffrement propre à cette technologie est considérée comme l’une des plus sûres à ce jour car toutes les données sont codées et sauvegardées avec un hachage cryptographique. Grâce à son architecture décentralisée, la stabilité des applications tierces est ainsi renforcée. En outre, avec la « Blockchain », un horodatage est attaché à chaque transaction, ce qui rend la manipulation des données et la redéfinition des opérations presque impossible. Seul bémol : les développeurs d’applications mobiles compétents maîtrisant la technologie « Blockchain » demeurent encore rares.
La sécurité des données d’une application mobile est un sujet central. Il doit être considéré en amont du développement jusqu’à la fin du cycle de vie de cette dernière, et ce, de manière continue.
Pour faire face à cet enjeu , il est essentiel de s’entourer d’experts en cybersécurité. Vous cherchez à consolider la sécurité de votre application mobile ? Discutez de votre projet avec nos spécialistes en cybersécurité !




