Mobile application security: vulnerabilities to watch out for
14/09/2021
7min
Tables des matières
Computer systems and computers aren't the only ones prone to security breaches: mobile devices and devices and applications are also highly vulnerable to cyberattacks.. Certain vulnerabilities are more frequent on this type of technical environment, and it is essential to detect them, from the creation phase of an application right through to the end of its lifecycle.
I - Security on Android and iOS: two rooms, two atmospheres
On the smartphone market, two operating systems predominate: iOS and Android. In June 2021, they will have a combined market share of 99.9% on the French market.
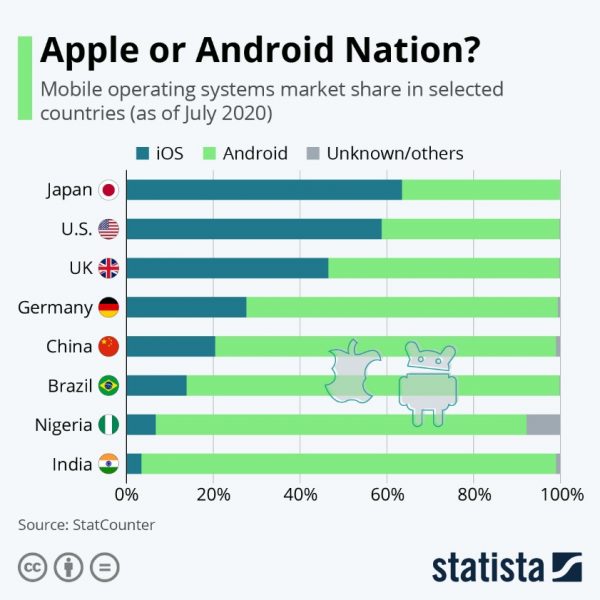
Source : Apple or Android Nation? Statista
These two operating systems have their own specificities in terms of application development. Indeed, while iOS applications are mainly programmed in Objective-C, Java is used on Android.
The same applies to their installation, configuration, programming environment, design, testing and management of the cybersecurity strategy.
II - The main types of vulnerabilities in mobile applications
Before listing the main vulnerabilities observed in mobile applications, it is important to remember that there are two categories of flaws in this type of software: unwanted behavior and vulnerability.
The unwanted behavior occurs unexpectedly by doing unnecessary actions in the background of the application.
We speak of vulnerability when the flaw does not result from a user's behavior but from the very structure of the application.
Vulnerability #1: lack of jailbreak detection
Jailbreak, also known as unjailbreaking or unlocking, is a process enabling a user to bypass the security restrictions of an operating system at its root. This method is particularly used on iOS to download applications that are not present on the official market (like Cydia, well known to " jailbreakers ").
Applications running in an unlocked environment remain more vulnerable and it is necessary to take this parameter into account when developing an application via jailbreak detection systems.
Vulnerability #2: Too little protection for transport protocols
The purpose of the TPC(Transmission Control Protocol) and IP(Internet Protocol) transport protocols is to transmit data from one machine to another.
Discover also 3 types of cyber-attack to which your company is exposed.
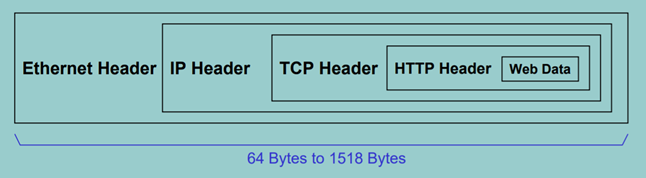
Source: Just how secure is the TCP/IP protocol?, BBC
Whether on the web or in an application, it's essential that data circulating between the different layers is secure. Without it, there is a risk of it being intercepted by malicious entities. To secure transport protocols, the best practice is to set up a data encryption process and host your applications on cloud.
Vulnerability #3: Authentication Breakdown
Broken authentication occurs when an attacker compromises an authentication system by stealing a password, session ID, login key or other login information. This common violation results in three types of attacks:credential stuffing,brute force access and sessionhijacking.
The consequences of a failure to authenticate can include data breach, identity theft or hijacking. To alleviate this problem, users should be forced to create complex passwords.
Vulnerability #4: Absence or invalidity of a security certificate
Securing applications also requires an encryption protocol. The SSL/TLS certificate is not limited to websites and also concerns mobile applications. However, many application servers do not have a valid SSL/TLS certificate.
Installing an SSL/TLS certificate on your server is essential and ensures that user data, both stored and in transit, remains protected and is not compromised.
Vulnerability #5: Lack of an Expiration Process
A session is the period of time that a user is active on your site or application. If an application's session expiration process is insufficient (or even non-existent), the user's account is exposed to attacks and the violation of their personal data.
It is therefore necessary to find a balance between UX (not asking the user to reconnect to make his experience less pleasant) and the security of the application.
Vulnerability #6: Poor control of data deserialization
In programmatic language, data deserialization is the act of extracting data from a stream and converting it into a format useful to the application. Deserialization engines are often the target of attacks. To avoid this, it is essential to always check the provenance of data and not to accept serialized objects from unapproved sources.
Vulnerability #7: Use of known vulnerable components
Not all components, frameworks and APIs are created equal when it comes to cyber security. Some APIs - even popular ones - are vulnerable to cyberattacks, and you should make sure they are reliable before integrating them into your application structure.
Vulnerability #8: Inadequate Cyber Security
When a cybersecurity strategy exists in the organization, the release of an application must, at a minimum, comply with the defined rules. However, it may happen that the strategy in place does not include rules specific to applications, or that it is imprecise or incomplete. In this case, it is necessary to define the security standard.
For example, a mobile backend can be set up. This involves setting up an intermediary space between data exchanges concerning the company and client-side security. The mobile backend will be the only access point for applications to the information system. It will generate alerts to IT teams in case of inappropriate use and will connect in a really secure way, for example via VPN, to the company's information system. For example, we can plan to set up a mobile backend. This means setting up an intermediary space between the data exchanges concerning the company and the security on the client side. The mobile backend will be the only access point for applications to the information system. It will generate alerts to IT teams in case of inappropriate use and will connect in a truly secure way, for example via VPN, to the company's information system.
Conclusion
Mobile applications are no exception to the growing demands of cybersecurity. To find out more, read our 5 best practices for securing mobile applications.
You have an application project and want to put all the chances on your side so that it is secure and efficient? Ask our cybersecurity specialists for advice!
Mobile application security: vulnerabilities to watch out for
14/09/2021
7min
Tables des matières
Computer systems and computers aren't the only ones prone to security breaches: mobile devices and devices and applications are also highly vulnerable to cyberattacks.. Certain vulnerabilities are more frequent on this type of technical environment, and it is essential to detect them, from the creation phase of an application right through to the end of its lifecycle.
I - Security on Android and iOS: two rooms, two atmospheres
On the smartphone market, two operating systems predominate: iOS and Android. In June 2021, they will have a combined market share of 99.9% on the French market.

Source : Apple or Android Nation? Statista
These two operating systems have their own specificities in terms of application development. Indeed, while iOS applications are mainly programmed in Objective-C, Java is used on Android.
The same applies to their installation, configuration, programming environment, design, testing and management of the cybersecurity strategy.
II - The main types of vulnerabilities in mobile applications
Before listing the main vulnerabilities observed in mobile applications, it is important to remember that there are two categories of flaws in this type of software: unwanted behavior and vulnerability.
The unwanted behavior occurs unexpectedly by doing unnecessary actions in the background of the application.
We speak of vulnerability when the flaw does not result from a user's behavior but from the very structure of the application.
Vulnerability #1: lack of jailbreak detection
Jailbreak, also known as unjailbreaking or unlocking, is a process enabling a user to bypass the security restrictions of an operating system at its root. This method is particularly used on iOS to download applications that are not present on the official market (like Cydia, well known to " jailbreakers ").
Applications running in an unlocked environment remain more vulnerable and it is necessary to take this parameter into account when developing an application via jailbreak detection systems.
Vulnerability #2: Too little protection for transport protocols
The purpose of the TPC(Transmission Control Protocol) and IP(Internet Protocol) transport protocols is to transmit data from one machine to another.
Discover also 3 types of cyber-attack to which your company is exposed.

Source: Just how secure is the TCP/IP protocol?, BBC
Whether on the web or in an application, it's essential that data circulating between the different layers is secure. Without it, there is a risk of it being intercepted by malicious entities. To secure transport protocols, the best practice is to set up a data encryption process and host your applications on cloud.
Vulnerability #3: Authentication Breakdown
Broken authentication occurs when an attacker compromises an authentication system by stealing a password, session ID, login key or other login information. This common violation results in three types of attacks:credential stuffing,brute force access and sessionhijacking.
The consequences of a failure to authenticate can include data breach, identity theft or hijacking. To alleviate this problem, users should be forced to create complex passwords.
Vulnerability #4: Absence or invalidity of a security certificate
Securing applications also requires an encryption protocol. The SSL/TLS certificate is not limited to websites and also concerns mobile applications. However, many application servers do not have a valid SSL/TLS certificate.
Installing an SSL/TLS certificate on your server is essential and ensures that user data, both stored and in transit, remains protected and is not compromised.
Vulnerability #5: Lack of an Expiration Process
A session is the period of time that a user is active on your site or application. If an application's session expiration process is insufficient (or even non-existent), the user's account is exposed to attacks and the violation of their personal data.
It is therefore necessary to find a balance between UX (not asking the user to reconnect to make his experience less pleasant) and the security of the application.
Vulnerability #6: Poor control of data deserialization
In programmatic language, data deserialization is the act of extracting data from a stream and converting it into a format useful to the application. Deserialization engines are often the target of attacks. To avoid this, it is essential to always check the provenance of data and not to accept serialized objects from unapproved sources.
Vulnerability #7: Use of known vulnerable components
Not all components, frameworks and APIs are created equal when it comes to cyber security. Some APIs - even popular ones - are vulnerable to cyberattacks, and you should make sure they are reliable before integrating them into your application structure.
Vulnerability #8: Inadequate Cyber Security
When a cybersecurity strategy exists in the organization, the release of an application must, at a minimum, comply with the defined rules. However, it may happen that the strategy in place does not include rules specific to applications, or that it is imprecise or incomplete. In this case, it is necessary to define the security standard.
For example, a mobile backend can be set up. This involves setting up an intermediary space between data exchanges concerning the company and client-side security. The mobile backend will be the only access point for applications to the information system. It will generate alerts to IT teams in case of inappropriate use and will connect in a really secure way, for example via VPN, to the company's information system. For example, we can plan to set up a mobile backend. This means setting up an intermediary space between the data exchanges concerning the company and the security on the client side. The mobile backend will be the only access point for applications to the information system. It will generate alerts to IT teams in case of inappropriate use and will connect in a truly secure way, for example via VPN, to the company's information system.
Conclusion
Mobile applications are no exception to the growing demands of cybersecurity. To find out more, read our 5 best practices for securing mobile applications.
You have an application project and want to put all the chances on your side so that it is secure and efficient? Ask our cybersecurity specialists for advice!




